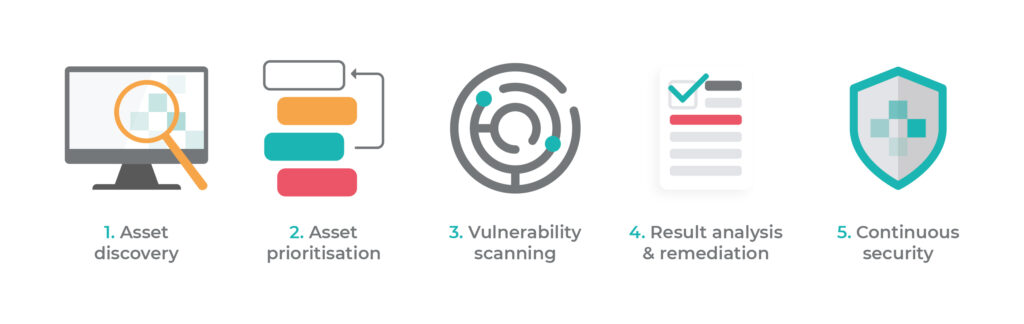
A vulnerability assessment is the process of defining, identifying, classifying and prioritizing vulnerabilities in computer systems, websites, applications and network infrastructures. Vulnerability assessments also provide an organization with the necessary knowledge, awareness and risk backgrounds to understand and react to threats to its environment. A vulnerability assessment process is intended to identify threats and the risks they pose. They typically involve the use of testing tools, whose results are listed in a vulnerability assessment report.
Organizations of any size, or even individuals who face an increased risk of cyber attacks, can benefit from some form of vulnerability assessment, but large enterprises and other types of organizations that are subject to ongoing attacks will benefit most from vulnerability analysis.
Because security vulnerabilities can enable hackers to access IT systems and applications, it is essential for enterprises to identify and remediate weaknesses before they can be exploited. A comprehensive vulnerability assessment, along with a management program, can help companies improve the security of their systems.
Security testing will never be an exact science where a complete list of all possible issues that should be tested can be defined. Indeed, security testing is only an appropriate technique for testing the security of web applications under certain circumstances. Our penetration test team will push your system to its limits in a barrage of simulated cyber attacks, discovering every possible vulnerability so that your organization gets the complete picture and 100% of your data is safe.